When we talk about security one of the things that is often overlooked or not fully calculated the actual risk. What is the actual risk you have as a company? What is it that is of value to you? What is it that you do not want to have leaked, exposed, or stolen? This is, in most cases, some sort of information. Information is the most valuable commodity we have. And since it has value, there is always a certain amount of risk associated with it.
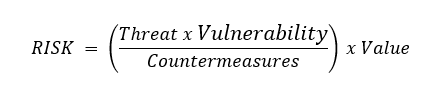
In order to calculate risk, you first need to know what it is that you have that you are considering valuable to your company and how much value this piece of information actually has. This could be the upfront cost that you paid for something, the time it took to develop, the future market value, and even how much it would cost to replace it. A hard drive is a relatively cheap item, but the information on it could potentially be worth billions, to you or even to someone else.
Threat as a risk factor
Threat is also a factor when calculating risk. What are the biggest threats you are facing? These range anywhere from natural disasters, corporate espionage, spies, disgruntled employees… Pretty much, if you are in any sort of business providing something that someone wants, then there is a good chance someone else wants to know what you know, or have what you have. Threats are the things that will do the damage to your organization.
Vulnerabilities are the entry point into the organization or enabling access to the information of value. Dealing with IT security, vulnerabilities can be exposure on the internet, easy access to the company network, or compromised client machines and servers. But vulnerabilities also include not checking everyone entering the building, unlock/unmonitored side entrances, losing or dropping information, or even a night out on the town with the executives. Never discount human error and ego. Drunk people like to talk and are not often aware of their surroundings. You never know when someone might be listening in on your conversations or going through the pockets of the coat that you checked in to the coatroom.
Made up Example:
Company X is a huge global company. They have offices and manufacturing spread all over the earth. They have grown very fast and have not kept up to date with their security (naughty naughty…). They of course have information that someone else might want, but also, they are a target just like every other business simply because they exist. What would happen if a small part of their business went down? Let’s say a region where they manufacture product Z. How many people would be affected? What would the costs be? Can we put a value on this attack? Yes, we can.
Read also: Security Awareness with Regards to External Third-Party Services Providers
This hypothetical attack knocked out the region with a good old crypto locker that found its way in from a targeted phishing campaign and relied on out-of-date systems which are missing much needed security patches.
The first cost we are looking at is the loss of production of what ever it is they are manufacturing. Let’s say their daily output values at €1,000,000 and they were down for 2 weeks! That is €10-14,000,000 in losses (depending on if they get the weekends off). And they are now behind so when they start again, they might need to increase their production to make up for that. But that is not the only cost at all. There will no doubt be people working around the clock to stop the attack, try to fix it and figure out what went wrong. Let’s just say that around 100 people were working like crazy for one month to contain and fix this so production could begin again. 100 people with an average cost of (lets estimate) €50/hour for the company, for 10 hours a day. That is an additional cost of €1,500,000! Just in people trying to contain this incident. Other costs could include replacement of equipment that might have been damaged.
Hidden costs
There are also a couple hidden costs you don’t immediately think about. Before the attackers let the crypto locker loose, did they steal any data as well? It’s possible that they stole some valuable information as well. Could this be a competitor that now knows your secrets? Or someone that is selling them to your competition? This could result is loss of business for you when someone is offering your product at a slightly reduced price.
The other hidden cost is brand damage. If the incident hits the news, this could cause customers to lose interest and not buy what ever it is they are trying to sell. This could potentially be the hardest to come back from.
Now, given that terrifying scenario, what could have been done to counteract this and how much would that have cost? Quick and dirty, they systems should have been kept up to date and patched as well as some email filtering and user security training. Let’s assume this would cost them an additional €2,000,000 a year in resources, software and equipment to mitigate the attack to a reasonable level. That is only €166,666 per month. When you consider that their loses exceeded €15,000,000 for one month, that is a small price to pay for prevention.
"The only people who claim they can provide you with complete security are fools or liars."
- Ira Winkler – Spies Among Us
For more great resources on this subject, please read Ira Winkler’s book "Spies Among US". Ira’s equation fixes a monetary value to the risk, which makes it a good motivator. Or Tony UcedaVelez’s book "Risk Centric Threat Modeling".
To sum up, businesses should be focusing more on their real risk and putting a monetary value to it. It is far too common that incidents like the example above actually happen. The costs can and have been great. But with a little planning for prevention, lots of these incidents can be drastically reduced. Certain things will always happen, and it is impossible to prevent every single attack, but there are many ways to catch it early and stop it before becoming too severe.


