As the Monty Python song goes, “Every [bit of information] is Sacred” … or something like that. If you think of bits of information as pieces of a puzzle, each new piece is possibly a new opportunity to connect larger pieces together. If you have enough pieces, before too long, you start to see the full picture.
This is the third part of our blog series about the dangers and vulnerabilities with public networks.
Read the first part of this blog series here: The Simple Dangers of Open Public Networks: Part 1 and the second part here: The Simple Dangers of Open Public Networks: Part 2.
Information begets more Information
From where we are at now, we have a company name and a username. This is not very special you might say, but these are two pieces of a puzzle that is your company. When it comes to usernames and computer names, this gives us a hint on how your naming standard is set up. For example: the username “denned”. Looking up employees of the company (on LinkedIn, Google, or the corporate website) might reveal some name. This palindrome can be reversed and found to be Dennis Nedry. This is a pretty standard process for a company to create usernames with. Similarly, computer names also tend to follow a standard. Such as: SE-STK-HR-007, which stands for Sweden-Stockholm-HR-James Bond. Next thing that we need to find out is now their email addresses are structured and we have good targets for a phishing campaign.
With the company’s name we can find the company’s domain name. And with this there is a lot of information that can be found. There are numerous open source information gathering tools online.
What all these tools do is enumerate the domain. They search records for all publicly available information regarding certificates distributed, URL’s, domains and subdomains, ports open, if there is an active HTTP server running, and even email addresses and servers. Some resources will also tell you if there are any known vulnerabilities associated with the current reported service, such as Shodan. From one root domain name, it is possible to expand that into thousands of external endpoints and potential targets.
There are also services such as haveibeenpwned and weleakinfo. These enable you to search through past data breaches for information and can contain very sensitive information such as accounts and passwords. A quick search with these services can tell you if any of your information has been found in a data breach recently, and if you should change your passwords.
What do you have exposed to the world at the moment? Do you know and keep a watch on it?
If the attacker had not been as lazy as we were, they would most likely have more information than this, including some password hashes which they would attempt to crack. In our experience, with a big enough dictionary list to run through, it is not uncommon to crack over 50% of the hashes fairly quickly. If you gathered 100 hashes, you could now potentially have 50+ valid usernames with passwords to use. (remember this for later…)
Breakdown
We have broken down the information we gathered into a more user-friendly format. Since we are mostly dealing with the companies, we decided to break it up into different sectors.
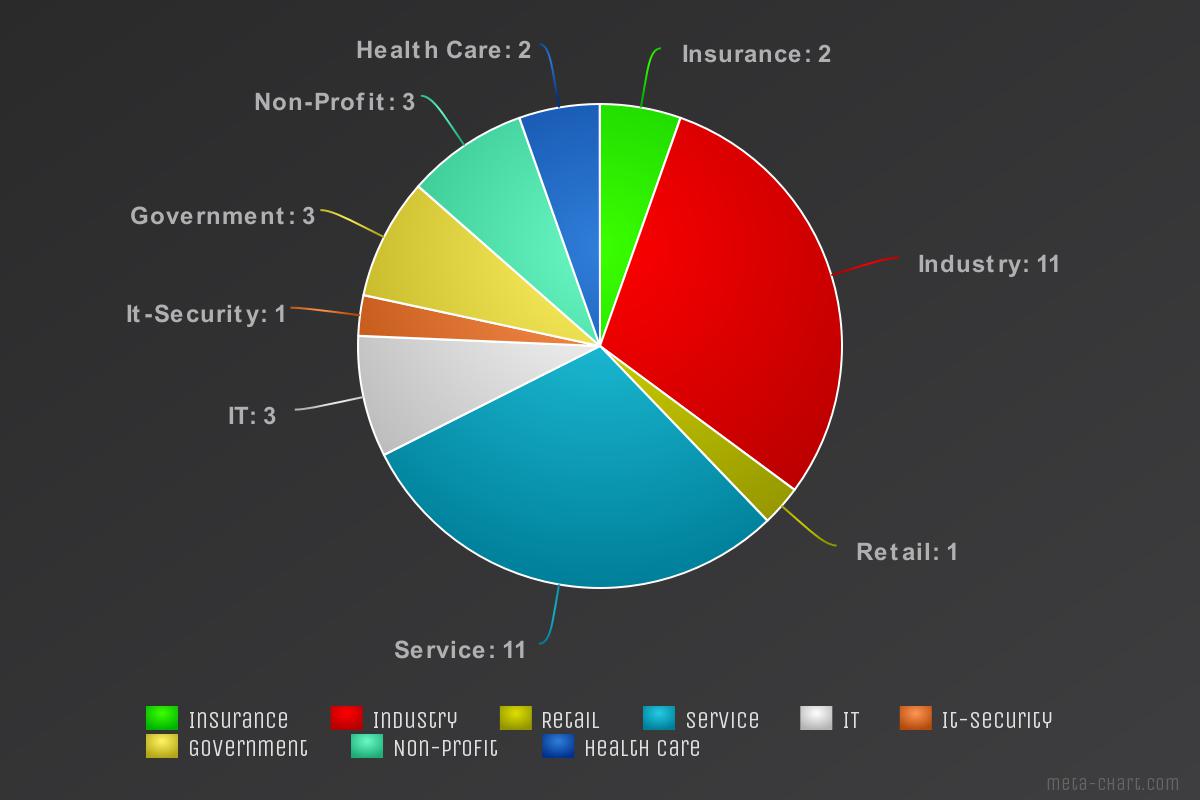
The chart above shows the number of companies that we were able to identify from our trips. Looking at the spread, we see that there was a little bit of everything. The major markets represented are the Industry and Service sectors with 11 companies from each. Government and health care also make a good representation. And one sector, IT-Security, should also be noted. No, it wasn’t us. 😊 But nobody is perfect.
Now let’s look at the same sectors, after a little bit of enumeration.
.jpeg?width=1200&name=External%20Exposure%20Pie%20(2).jpeg)
The chart above shows the average number of subdomains found per company in each sector. As we can see, there is one sector that grew drastically: Retail. Now, given the sample size was only one company, this is should not be considered statistically significant and does not represent all retail companies. However, it is a good example of what can happen. From one company, we see 1424 subdomains. The attack surface has grown significantly.
With a little more searching, what can we find?
So, what kind of services are being exposed by all these companies? Looking through the results we find HTTP services, API’s, FTP servers, Databases, Administration applications, VPN gateways, etc. Along with thousands of web applications, many of which are no longer used or out of date.
With a little digging and some open source intelligence work, we have greatly expanded the potential attack surfaces of all these companies. This is not saying that there is any increased risk by finding this information. It is all public knowledge anyway. But it does add a lot of pieces to the puzzle.
From where we stand now; we have users, names, maybe some email addresses, lots of services, and if the attack was real, there would possibly be some passwords to go with those accounts as well. This is where it gets a bit frightening.
Now, we found these users outside of their domain, right? Which means there is a good chance they have access to some of the resources inside of their domain, from the outside. As in, they might have valid login credentials to some of these services. Good for a hacker, very bad if it’s you though.
One particular service that would be targeted first would be the company’s VPN portal. The attacker and the company both view the VPN service in different way. The company sees it as an easy way to access internal resources. The attacker sees it as an easy way to access internal resources. Yes, those are the same, but they are coming from very different mindsets. The company wants to provide a way for its employees to be more productive and providing a secure way to do it. If the attacker can get in this way, he has significant access to internal resources and has just breached your security perimeter.
Worse case
In a worst-case scenario, the attacker would be on that train, grabbing all the hashes they can. After cracking as many as time allows, they proceed to enumerate the domains and find VPN portals that are exposed. Ones that do not have multi-factor authentication enabled. They log in, and now have access as a legitimate user. From here, they can start to map out the rest of the network, file shares, databases, etc. All the while continuing to compromise more users and servers until they come across a domain administrator. If they were lucky, and quiet enough not to trip any security measures, it is game over and now they have complete control of your domain.
All because someone was on a train…
This is a bit of an over-simplified scenario of how it works. But when you boil it down, it does come down to those simple steps.
Kategori:Säkerhet
This article is a part of a summary on what we found and how to improve in your organization’s security as well as the awareness of employees.
Read the full report here:


